7SIGNAL utilizes Single sign-on (SSO) and OAuth 2.0 to verify identity and authenticate users before they may access Mobile Eye and Sapphire Analyzer. It works with any internet accessible SAML or OAuth-based identity solution.
At this time, 7SIGNAL only supports Service Provider Initiated (SP-initiated) SSO. This gives your end users the ability to sign into 7SIGNAL Mobile Eye login page, which initiates an authorization request to the Identity Provider (e.g. Okta, OneLogin, or Microsoft Azure AD). Once the IdP authenticates the user's identity, the user is redirected and automatically logged into the user interface.
A current list of supported identity management providers is below and 7SIGNAL must have your email address (not your password) before you attempt to login.
- Microsoft
- Okta
- OneLogin
If you do not use one of the identity management providers listed above, then integration steps are required. Exchange SAML metadata files with 7SIGNAL as an initial first step towards SSO integration.
Microsoft ADFS
7SIGNAL ADFS v3 Configuration Guide
7SIGNAL ADFS v4 Configuration Guide
Microsoft Azure Enterprise Application Setup (OAuth)
- Login to the Microsoft Azure portal as a Global Administrator at https://portal.azure.com
- From the left navigation bar, select ‘Azure Active Directory’, then ‘Enterprise applications’
- Click ‘New application’, select ‘Non-gallery application’
- Assign a name such as, 7SIGNAL Mobile Eye, then click ‘Add’
- On the new App, select Single sign-on from the left, then select SAML-based Sign-on
- Edit ‘Basic SAML Configuration’
- You’ll need to add https://login.7signal.com/mobile as Identifier and https://login.7signal.com/auth/saml/acs as the Reply URL. Click Save.
- Download the Federation Metadata XML file from the links on the same page and provide it to 7SIGNAL
- Click Users and groups. Assign the appropriate users or groups. That’s it!
Here’s the Microsoft document that reviews the general process.
Granting Admin Consent
For Office 365 and Azure Active Directory, some organizations do not allow users to grant their own permission and verify their own identity to applications. Instead, they require consent from a Azure Global Administrator and may be prompted for approval (see below).
To grant consent to access Mobile Eye on behalf of users in their organization, Azure Global Administrators need to login then click the link below to complete the process:
OKTA Setup
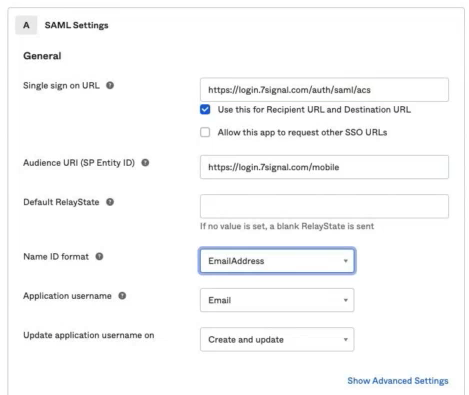
Please send 7SIGNAL the following:
- Your Identity Provider Single Sign-On URL
- Identity Provider Issuer URL
- Your X.509 Certificate
- Your SAML Metadata file